Suppose you are trying to troubleshoot a site to site VPN tunnel that is designed like this:
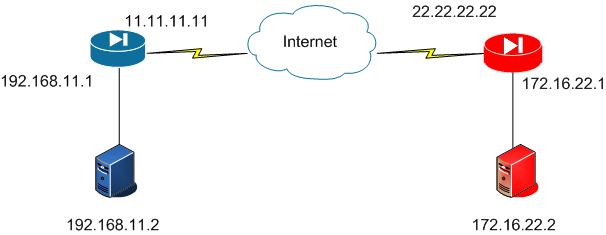
Upon doing show ipsec sa peer on the blue ASA you see the following:
|
The problem above shows that Phase 1 of the tunnel is successfully establishing but phase 2 has problems. Specifically the firewall is encrypting packets but not decrypting them.
If an ASA or router is getting encaps but not decaps, this means it is encrypting the data and sending it but has not received anything to decrypt in return.
- Verify the other end has a route outside for the interesting traffic.
- Check that both VPN ACL’s are not mismatched.
- Double check NAT’s to make sure the traffic is not NAT’ing correctly.
- Is what you are trying to ping even responding back? Often what you’re sending traffic to is not able to accept or is not responding to this traffic. I prefer to put a packet capture on the remote end firewall to see if the traffic is coming back into that firewall.
Comments