Have you ever wondered what the flags meant when you issued the show conn or show connections command? This post will demystify that for you.
Viewing the Connections
Use the command show conn to view the connections currently going through the firewall. It should look something like this:
|
Understanding the Flags
In earlier versions of Cisco ASA versions it used to list the following table when issuing the show conn command.
- A – awaiting inside ACK to SYN
- a – awaiting outside ACK to SYN
- B – initial SYN from outside
- C – CTIQBE media
- D – DNS
- d – dump
- E – outside back connection
- F – outside FIN
- f – inside FIN
- G – group
- g – MGCP
- H – H.323
- h – H.225.0
- I – inbound data
- i – incomplete
- k – Skinny media
- M – SMTP data
- m – SIP media
- O – outbound data
- P – inside back connection
- q – SQL*Net data
- R – outside acknowledged FIN
- R – UDP RPC
- r – inside acknowledged FIN
- S – awaiting inside SYN
- s – awaiting outside SYN
- T – SIP
- t – SIP transient
- U – up
Adding it up
Often a single flag isn’t seen, but multiple flags will be displayed. Use this handy guide to understand flag combinations.
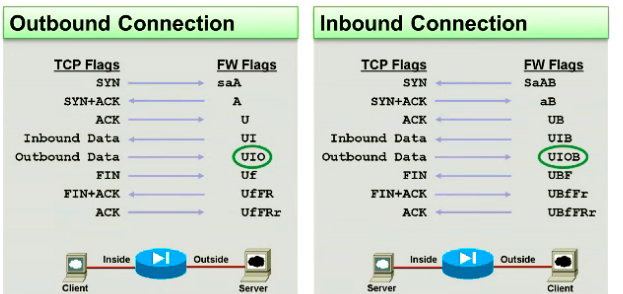
The green circles in the image above indicates two way traffic is seen for that connection which means the connection is good and healthy usually.
Case Studies
Let’s look at a few examples. Suppose you see the lines in the ‘show conn’ output.
|
This traffic flow has completed the 3 way TCP handshake (U), has had both inbound (I) packet and outbound (O) packets.
|
This traffic flow originated from the outside (B), has completed the 3 way TCP handshake (U), has had both inbound (I) packet and outbound (O) packets. This flow also saw a fin packet sent to the inside (f) and the inside also acknowledged the fin ®.
|
This flow has no flags because it’s a UDP packet and therefore is stateless.
|
This flow is just completing the 3 way handshake (U).
|
A SYN was sent from 10.20.20.20 on the inside to 10.30.30.30 on the outside.
|
A SYN+ACK has been seen coming from the outside coming in.
Comments